Red Ice Creation’s Henrik Palmgren documents why Pirate Bay Co-founder Gottfrid Svartholm Warg currently is in solitary confinement in Denmark. Please support political prisoners however you can.
Red Ice Creation’s Henrik Palmgren documents why Pirate Bay Co-founder Gottfrid Svartholm Warg currently is in solitary confinement in Denmark. Please support political prisoners however you can.

[1] The two circles near the center of the artifact appear to be earth. [2] This appears to be a spacecraft of some type. [3] This appears to be a massive comet or asteroid headed toward earth. [4] Appears to be a specially designed spacecraft capable of deflecting a large comet or meteor, such as NASA “Deep Impact”. [5] Appears to be an astronaut in control of a craft. [6] What appears to be an intelligently controlled spacecraft.
CALAKMUL, MEXICO (INTELLIHUB) — Newly released Mayan documents, i.e. artifacts, dating back at least 1300-years reveal that the human race is not alone and highly advanced technologies including space travel have likely existed for quite some time.
Not only does this documentation released by the Mexican government show the existence of an explorer race, it may also reveal the roots of mankind.
Some consider the government’s presentation of the information to be a major step forward for humanity as the truth is finally being slowly let out. Hopefully this will prompt other governments around the world to be more forthcoming with such information, turning the tide in the UFO and extraterrestrial research community for good.
Sundance winner Juan Carlos Rulfo’s Revelations of the Mayans 2012 and Beyond also touches on such technology. “Producer Raul Julia-Levy said the documentary-makers were working in cooperation with the Mexican government for what he said was “the good of mankind”. He said the order to collaborate had come directly from the country’s president, Álvaro Colom Caballeros.
“Mexico will release codices, artefacts and significant documents with evidence of Mayan and extraterrestrial contact, and all of their information will be corroborated by archaeologists,” he said. “The Mexican government is not making this statement on their own – everything we say, we’re going to back it up.”
Caballeros himself was conspicuous by his absence from the statement released by Julia-Levy. So far, the minister of tourism for the Mexican state of Campeche, Luis Augusto García Rosado, appears to be the highest-ranking government official to go on record confirming the discovery of extraterrestrial life, but he’s not holding back.
In a statement, Rosado spoke of contact “between the Mayans and extraterrestrials, supported by translations of certain codices, which the government has kept secure in underground vaults for some time”. In a telephone conversation with the Wrap, he also spoke of “landing pads in the jungle that are 3,000 years old”.[2]
These secrets have been said to be “protected” by the mexican government for as long as 80-years.

Australia’s ABC News 24 reports that fast food is trying to kill your brain:
A team of researchers from the University of New South Wales has uncovered a link between junk food and memory loss. The team placed rats on a diet high in sugar and fat and compared their performance with rodents on a healthy diet.
Lead researcher Margaret Morris says the rats on the poor diet developed an impaired memory after just six days. “Poor diet was associated with a cognitive decline that happened very quickly,” she told AM.
Professor Morris says the memory issues became apparent well before the animals showed any physical symptoms. “The animals of course weren’t obese after just six days on the diet. So the changes in cognition, the loss of memory, happened well before there was any weight change,” she said.
Researchers have demonstrated the ability to remotely hack into a MacBook webcam without triggering the indicator light, a capability which the FBI has reportedly had for several years.
In August, it was revealed that the National Security Agency (NSA) calls on its employees to physically remove the built-in webcam from Apple laptops for security reasons.
The findings of the researchers, first reported on by The Washington Post, are especially interesting because Apple laptops have the indicator LED hardwired to the camera.
This hardwiring is designed to activate the light whenever the camera is activated, a feature that should prevent the remote activation of the webcam without the user’s knowledge.
The researchers looked at 2008 MacBooks and MacBook Pros, so it is unclear if the results also apply to today’s Apple laptops.
The researchers from Johns Hopkins University told the Post that “similar techniques could work on more recent computers from a wide variety of vendors.”
“In other words, if a laptop has a built-in camera, it’s possible someone — whether the federal government or a malicious 19 year old — could access it to spy on the user at any time,” the Post reports.
Stephen Checkoway, a computer scientist at Johns Hopkins who co-authored the study, found a way to remotely reprogram the iSight camera’s micro-controller chip that is supposed to establish a hardware-level interlock between the camera and the indicator light, according to The Verge.
The researchers provided the Post with a copy of their proof-of-concept software, demonstrating how the camera can be remotely activated without turning on the indicator light.
“People are starting to think about what happens when you can reprogram each of those,” said Charlie Miller, a security expert working for Twitter, referring to micro-controllers like the one attached to the iSight camera.
Miller cited an attack that could rapidly discharge Apple batteries via the micro-controller, which could potentially lead to a fire or even an explosion.
Using a similar method, another researcher demonstrated how the built-in Apple keyboard could be turned into spyware.
While the paper only cites the earlier generation of Apple products, Miller contends that similar attacks could apply to new Apple systems.
“There’s no reason you can’t do it — it’s just a lot of work and resources but it depends on how well [Apple] secured the hardware,” Miller said to the Post.
Apple did not reply to the Post’s requests for comment, but what is more troubling is the response the researchers received from company representatives.
“Apple employees followed up several times but did not inform us of any possible mitigation plans,” the researchers wrote in the study.
While Apple supposedly has the indicator light hardwired to the camera, many others do not offer such a feature.
“Logitech cameras, for example, have a software-controlled LED,” Ars Technica reports. However, this is designed to work with a software feature that allows them to be used as motion-activated security cameras.
“Whether this design makes sense for most users, given the apparent abundance of surreptitious webcam-based spying, is less clear,” notes Peter Bright for Ars Technica.
On a positive note, secure designs for the indicator light are indeed possible but software-mediated hardware interlocks for indicator lights remain vulnerable.
Ars sums it up quite rightly in saying, “When it comes to protecting against webcam spying, you should ignore the technology and simply tape over the camera.”
Ever wondered why you can’t find a post from your favorite alternative media website on the world’s most famous search engine?
The Register is reporting a pressure surge from politicians, judges, cops and the like to remove material from Google that’s critical of them:
Today, the advertising giant said that, in the first six months of 2013, it received 3,846 demands from public officials to remove 24,737 personal blog posts, YouTube videos and other pieces of content it hosts. That’s up 68 per cent on the second half of 2012.
And according to the web giant, which has just published its latest transparency report, 93 requests focused on content that was critical of people in public office. Defamation and copyright infringement were often cited, but less than one third of the highlighted material was removed in the first half of 2013.
A whopping 93% of the requests — basically all of them — were attempting to censor people who are critical of public officials on the web. While some content may actually be defamation, just how gray are the lines surrounding that definition?
In the U.S., requests were up 70% and included 27 federal agency requests to pull apps from the Google Play store for trademark infringement. As for the U.K., Google wrote, “We received a request from a law firm representing a former Member of Parliament to remove a preview from Google Books that allegedly defamed the MP by suggesting he was engaged in illegal activity. We removed the preview.”
Google legal director Susan Infantino wrote that these requests have become a consistent and “worrying trend” for the past four years. Worrying trend or slippery slope to a politically correct nightmare?
In 2012, the Internet Society took of poll of more than 10,000 Internet users from over 20 countries around the world and found that the majority of them (86%) strongly agreed that “Freedom of expression should be guaranteed on the Internet.”
But free expression isn’t guaranteed. In fact, depending on what country you live in, the Internet landscape can look like a very different place — one with a whole lot of “filtering” going on.
Take China for example. If you live in China, you are not allowed to access social networking sites like Facebook or Twitter. They are just blocked, period. Information that might embarrass the Chinese government, such as information on the Tiananmen Square Massacre during which the government implemented martial law and killed thousands of pro-democracy protestors, simply does not exist on the Internet when accessed in China. It’s as if none of that stuff ever happened. China has essentially erased the online history books.
That’s what happened in George Orwell’s 1984 when history was literally erased and rewritten to a Big Brother-centric point of view.
And that is exactly what our so-called leaders would love to do to our Internet all over the world. Silence political dissent.
Don’t believe it? Check out the Stratfor email posted on Wikileaks claiming that CIA Director John Brennan is behind a witch hunt for “anyone printing materials negative to the Obama agenda”. (Probably not gonna find that link with a Google search…)
It’s sad we live in such an Orwellian time that politicians can just get whole chunks of the Internet they do not agree with (or that do not agree with them) erased, much like the Ministry of Truth rewriting history in the book 1984… which was a novel, not an instructional manual, for the record.

Security researchers have successfully broken one of the most secure encryption algorithms, 4096-bit RSA, by listening – yes, with a microphone — to a computer as it decrypts some encrypted data. The attack is fairly simple and can be carried out with rudimentary hardware. The repercussions for the average computer user are minimal, but if you’re a secret agent, power user, or some other kind of encryption-using miscreant, you may want to reach for the Rammstein when decrypting your data.
This acoustic cryptanalysis, carried out by Daniel Genkin, Adi Shamir (who co-invented RSA), and Eran Tromer, uses what’s known as a side channel attack. A side channel is an attack vector that is non-direct and unconventional, and thus hasn’t been properly secured. For example, your pass code prevents me from directly attacking your phone — but if I could work out your pass code by looking at the greasy smudges on your screen, that would be a side channel attack. In this case, the security researchers listen to the high-pitched (10 to 150 KHz) sounds produced by your computer as it decrypts data.
This might sound crazy, but with the right hardware it’s actually not that hard. For a start, if you know exactly what frequency to listen out for, you can use low- and high-pass filters to ensure that you only have the sounds that emanate from your PC while the CPU decrypts data. (In case you were wondering, the acoustic signal is actually generated by the CPU’s voltage regulator, as it tries to maintain a constant voltage during wildly varied and bursty loads). Then, once you have the signal, it’s time for the hard bit: Actually making sense of it.
Without going into too much detail, the researchers focused on a very specific encryption implementation: The GnuPG (an open/free version of PGP) 1.x implementation of the RSA cryptosystem. With some very clever cryptanalysis, the researchers were able to listen for telltale signs that the CPU was decrypting some data, and then listening to the following stream of sounds to divine the decryption key. The same attack would not work on different cryptosystems or different encryption software — they’d have to start back at the beginning and work out all of the tell-tale sounds from scratch.
The researchers successfully extracted decryption keys over a distance of four meters (13 feet) with a high-quality parabolic microphone. Perhaps more intriguingly, though, they also managed to pull of this attack with a smartphone placed 30 centimeters (12 inches) away from the target laptop. The researchers performed the attack on different laptops and desktops, with varying levels of success. For what it’s worth, the same kind of electrical data can also be divined from many other sources — the power socket on the wall, the remote end of an Ethernet cable, or merely by touching the computer (while measuring your body’s potential relative to the room’s ground potential).

In this light-weight setup, only the microphone (B) needs to be positioned correctly — everything else could be hidden away, for stealthy snooping
In terms of real-world repercussions, acoustic cryptanalysis is actually surprisingly dangerous. Imagine if you were decrypting some files in a library, coffee shop, or other public space — someone could obtain your decryption key just by placing their phone near your computer. Alternatively, an attacker could use spear phishing to put malware on your phone that listens for the decryption key. With HTML5 and Flash able to access the microphone, it would be possible to build a website that listens for encryption keys too. The researchers propose one particularly nefarious scenario: Put a microphone into a co-located server, slot it into a rack in a data center, and then scoop up the encryption keys from hundreds of nearby servers.
If you want to keep your data secure, you only really have two viable options: Heavy-duty encryption, physical security, and ideally both at the same time. If an attacker can’t get physically close to your data, it instantly becomes much harder to steal it. As far as mitigating acoustic cryptanalysis attacks, you either implement physical security — keep your laptop in a sound-tight box, or never let anyone near your computer when you’re decrypting data — or you need to use a “sufficiently strong wide-band noise source.” Something like a swooping, large-orchestra classical concerto would probably do it.
Research paper: RSA Key Extraction via Low-Bandwidth Acoustic Cryptanalysis [PDF]
The “Internet of Things” just wouldn’t be “Internet” enough if Google was not involved in a major way. Fortunately for those who have designed the gadget spy system, however, Google is attempting to become heavily involved in the implementation of yet another piece of the technological control grid.
According to the The Information and The Verge, Google is now testing thermostats connected to the Internet that would allow users to view the amount of energy being consumed in their homes as well as be able to make adjustments to that level of consumption. At least that is the justification used to sell the technology to the public. The real reasons behind both Google’s foray into the relatively new field and those of other tech firms, governments, and “sustainability”-related organizations are somewhat less interested in consumer satisfaction, environmental health, and lower energy bills.
Google’s latest foray into the control grid, a wide open country for the corporate giant which never seems tired of pioneering new marketable technological control products, is called EnergySense. This new program is round two for Google, which attempted something similar a few years ago named Powermeter, although this program was terminated in mid-2011 due to “difficulties scaling it up.” The mission statement for Powermeter, similar to that of EnergySense “was that people could trim energy use by 15 percent if they could see what was happening.”
Things are looking up for Google in this regard, however, as Josh Lowensohn of The Verge writes that “This might be a better time for such a service, as indicated by a rising wave of connected home appliances. That includes Nest, which began with thermostats and has since moved onto smoke detectors. It’s joined by a host of Wi-Fi and Bluetooth-connected appliances that can pipe information to the cloud, from refrigerators to web cameras.”
Interestingly enough, Google Ventures already invested in Nest in 2012.
Of course, if one is better able to monitor and observe the amount of energy being used by a household or appliance, it stands to reason that one would be better able to reduce and conserve the amount of energy he uses. However, are we really expected to believe that Google simply wants consumers to be better able to monitor their energy use to save money and the environment? Or is Google interested in something else entirely?
The Verge’s Josh Lowensohn may be on to more than he knows when he writes that “For Google, and others, those devices represent a possible wealth of data.”
Data, indeed. Google’s latest “new” venture is but one more step in the merger between the “Internet of Things” and the “Smart Grid,” the solidification of the surveillance state and eco-fascism into one entity that itself is only part of a much larger agenda.
For those who are unaware of what the term “Smart Grid” means, the Smart Grid is essentially a computerized system that allows the monitoring and control over energy use from power at the plant source to every appliance in the home. Smart Grid technology is a major part of UN Agenda 21, the United Nations’ plan to herd a drastically reduced population into “human habitat areas,” meaning ultra-modern super cities with stack em’ and pack em’ dwelling structures and zero contact with nature and the outside world.
The “Internet of Things,” of course, is the term used by disgraced former General and CIA Director David Petraeus to describe the rise of gadgets which are connected and controlled by apps.Petreaus himself discussed the fact that, because of this new technology, intelligence agencies will no longer need to place spy devices inside your home – you will do it for them.
As I wrote in my article, “New Report: ‘Recording Everything’ Details How Governments Can Shape The Dynamics Of Dissent,” within the next few years, it will be possible for the intelligence wing of the U.S. government to collect, store, and centralize every type of data in existence on every human being in the country, 24 hours a day, seven days a week, for one year for a total cost ranging in the few hundred thousands. And this is only what has been announced. It doesn’t include the secret black projects that currently remain under wraps or the fact that these programs have been ongoing for years.
Not only that, but with the open desire by the U.S. government to create a Total Information Awareness network, as well as the legal infrastructure such as the Patriot Act and other Big Brother legislation, a climate has been created where all of the data acquired by “Smart” appliances will inevitably be soaked into this government network. Not only that, the snooping infrastructure is such that one can assume that every piece of information that finds its way into the Cloud will not eventually find its way to a centralized government database, but will do so immediately.
The fact is, while even those few individuals who are still concerned with their privacy complain about their constant loss of it, the all-too-familiar warning of our descent into a world spoken of in George Orwell’s 1984 is often repeated ad nauseum. However, one need only look around to understand that we are not in danger of turning into the Orwellian surveillance state in the near future. We are already in it.
—————
Brandon Turbeville is an author out of Florence, South Carolina. He has a Bachelor’s Degree from Francis Marion University and is the author of six books, Codex Alimentarius — The End of Health Freedom, 7 Real Conspiracies, Five Sense Solutions and Dispatches From a Dissident, volume 1and volume 2, and The Road to Damascus: The Anglo-American Assault on Syria. Turbeville has published over 275 articles dealing on a wide variety of subjects including health, economics, government corruption, and civil liberties. Brandon Turbeville’s podcast Truth on The Tracks can be found every Monday night 9 pm EST at UCYTV. He is available for radio and TV interviews. Please contact activistpost (at) gmail.com.
Major tech corporations such as Facebook, Google, Microsoft and Amazon are purchasing fiber optic cables used for the internet to become the suppliers of the information, servicing the internet themselves.
When a user visits Amazon.com, they are standing on private digital property and are subject to the rights and laws where the servers are housed.
This enables the governments, through direct contact with the literal connections to the internet via these corporations, the systematic control over the free flow of information continues on.
Regardless of SOPA, PIPA, ACTA or any other legislator action by governments, the ability for users to maintain their 1st Amendment rights on the internet is being placed into the hands of the corporations.
Google already owns more than 100,000 miles of global private FOC routes.
Facebook has recently installed a network that connects user information to the Arctic Circle Datacenter (ACD).
Both Microsoft and Amazon have invested in cloud services.
Google’s Project Link (PL) wants to build “fiber-optic networks, making it possible for local providers to connect more people to the Internet and each other.”
To attain the goal of creating a “faster, more reliable internet” PL is seeking to construct “fiber-optic networks” that “enables internet service providers (ISPs) and mobile operators to provide faster connections.”
Google said: “Beyond basic access, local providers will be able to offer new mobile data plans or high-speed Internet to support new services. With a fast fiber-optic network in Kampala, for instance, ISPs can better support the city’s entrepreneurs.”
This ideal location comes complete with high-speed undersea cables.
To solidify their influence over government, the titans of the internet, including Google, eBay, Amazon and Facebook, combined forces under the blanket of a newly formed lobby group that wants to influence lawmakers on how they can manipulate the internet as well as how important they truly are.
The lobby group is called the Internet Association , and is based in Washington, DC, and headed by Michael Beckerman, former adviser of the Energy and Commerce Committee within the House of Representatives.
The Internet Association’s goal is to control the perspective of elected officials on internet technologies, their uses and cooperation with various federal agencies. Their website claims they are “dedicated to advancing public policy solutions to strengthen and protect an open, innovative and free Internet.”
Beckerman explains : “The Internet isn’t just Silicon Valley anymore. The Internet has moved to Main Street. Our top priority is to ensure that elected leaders in Washington understand the profound impacts on the Internet and Internet companies on jobs, economic growth, and freedom.”

I won't hold you in suspense with this article: The Ark of Noah has been found. It's real. I'll describe the evidence in some detail and end with the historical and religious implications.
How It Was Discovered
In 1959, Turkish army captain Llhan Durupinar discovered an unusual shape while examining aerial photographs of his country. The smooth shape, larger than a football field, stood out from the rough and rocky terrain at an altitude of 6,300 feet near the Turkish border with Iran.

Photo: http://www.viewzone.com/noahx.html
Capt. Durupinar was familiar with the biblical accounts of the Ark and its association with Mount Ararat in Turkey, but he was reluctant to jump to any conclusions. The region was very remote, yet it was inhabited with small villages. No previous reports of an object this odd had been made before. So he forwarded the photographic negative to a famous aerial photography expert named Dr. Brandenburger, at Ohio State University.
Brandenburger was responsible for discovering the Cuban missile bases during the Kennedy era from reconnaissance photos, and after carefully studying the photo, he concluded: "I have no doubt at all, that this object is a ship. In my entire career, I have never seen an object like this on a stereo photo."

Photo: http://www.viewzone.com/noahx.html
In 1960 the picture [above] was published in LIFE magazine under the heading of Noahs Ark? That same year a group of Americans accompanied Capt. Durupinar to the site for a day and a half. They were expecting to find artifacts on the surface or something that would be unquestionably related to a ship of some kind. They did some digging in the area but found nothing conclusive and announced to the anxiously waiting world that it appeared to be a natural formation.
Most of the global media turned away from the find and it became a non-story.
In 1977 Ron Wyatt visited the site. Obtaining official permission, Ron and others conducted more thorough research over a period of several years. They used metal detection surveys, subsurface radar scans, and chemical analysis -- real science -- and their findings were startling. The evidence was undeniable. This was the Ark of Noah.
The Visual Evidence
The first part of the survey was to examine the object and take its measurements. The shape looked like hull of a ship. One end was pointed as you would expect from bow [below: D] and the opposite end was blunt like a stern. The distance from bow to stern was 515 feet, or exactly 300 Egyptian cubits. The average width was 50 cubits. These were the exact measurements mentioned in the Bible.

Photo: http://www.viewzone.com/noahx.html
On the starboard side (right) near the stern there were four vertical bulges protruding from the mud [B], at regular intervals, that were determined to be the "ribs" of the hull [see below]. Opposite to these, on the port side, a single rib [A] protrudes from the mud. You can see its curved shape very clearly. Surrounding it are more ribs, still largely buried in the mud, but visible upon close examination.
Remember that this object, if it is the Ark, is extremely old. The wood has been petrified. Organic matter has been replaced by minerals from the earth. Only the shapes and traces of the original wood remain. Perhaps this is why the expedition in 1960 was disappointed. They anticipated finding and retrieving chucks of wood, long since eroded.
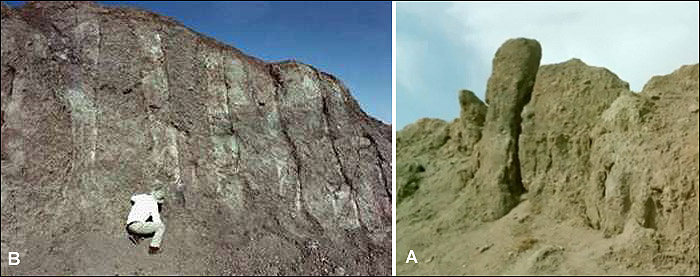
Photo: http://www.viewzone.com/noahx.html
From the position of the object in the middle of an obvious mud flow, it is obvious that the object slid down more than a mile from its original location. Geologists believe it was originally over 1000 feet higher in the mountain and encased in a shell of hardened mud. They think that an earthquake in 1948 cracked the mud shell and revealed the structure. This is confirmed by stories from the surrounding villagers who tell of its "sudden appearance" around that time.
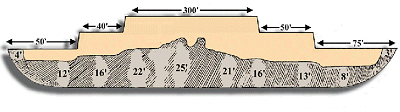
Photo: http://www.viewzone.com/noahx.html
Biblical accounts of the Ark describe it as having as many as six levels. The assumed shape of the Ark seems consistent with the bulge [C] in the middle of the object. In fact, as we will soon learn, radar scans of the structure suggest that this bulge is the collapsed debris of these levels.
Although most people think of the Ark as being rectangular, that only applies to the top decks. The sleek shape of the hull is necessary to enable the huge ship to remain stable in the water and survive tremendous waves.
Ground Penetrating Radar
The human eye needs to see reflected light to recognize an object. To visualize what remains below the earth, scientists use microwaves which can penetrate the ground and bounce back when they hit something solid. This technique is commonly used to locate oil and other minerals. Called Ground Penetrating Radar (GPR), the apparatus us made from an antenna that transmits, then listens to receive the "echo" and prints the result on a piece of paper. The delay and strength of this echo tell the geologists how solid and at what depth the objects are under the earth.
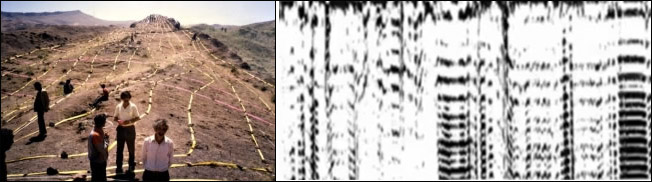
Photo: http://www.viewzone.com/noahx.html
The team of geologists didn't scan the entire object. Instead, they marked out lines that crossed the object with yellow tape. Then they dragged the antenna (about the size of a lawnmower) over the lines and watched the output on the paper recorder. When they got a strong "hit" -- meaning there was something solid underneath -- they would record the position on the tape [above]. Later, when they made a map of the object, the tape and the location of the "hits" they realized that there was indeed a structure underneath the mud.
"This data does not represent natural geology. These are man made structures. These reflections are appearing too periodic... too periodic to be random in that type of natural pace." - Ron Wyatt of SIR Imaging team

Photo: http://www.viewzone.com/noahx.html
The radar cans revealed this structure [above] under the mud. The symmetry and logical placement of these objects shows that this is unmistakably a man made structure, most likely the Ark of Noah.
Artifacts Retrieved From The Ark
Using the GPR, Ron Wyatt discovered an open cavity on the starboard side. He used an improvised drill to make core sample inside this cavity and retrieved several very interesting objects. Below you can see the artifacts which were sent for laboratory analysis. On the left is the bore hole [see below], followed by what turned out to be petrified animal dung, then a petrified antler and lastly a piece of cat hair.

Photo: http://www.viewzone.com/noahx.html
Perhaps the most significant find from the Ark itself is a piece of petrified wood. When this was first found it appeared to be a large beam. But upon closer examination it is actually three pieces of plank that have been laminated together with some kind of organic glue! This is the same technology used in modern plywood. Lamination makes the total strength of the wood much greater than the combined strength of the pieces. This suggests a knowledge of construction far beyond anything we knew existed in the ancient world.

Tests by Galbraith Labs in Knoxville, Tennessee, showed the sample to contain over 0.7% organic carbon, consistent with fossilized wood. The specimen was once living matter. Photo: http://www.viewzone.com/noahx.html
Examination reveals the glue oozed from the layers. The outside of the wood appears to have been coated with bitumen.
Even more surprising were laboratory analyses which not only revealed that the petrified wood contained carbon (proving it was once wood) but there were iron nails [above right] embedded in the wood!
We like to imagine that humanity evolved in a neat sequence of eras, each named after the technology that was discovered. We have the Stone Age (where man developed arrows and stone tools), the Bronze Age (where metals were combined and heated to make tools and household items) and lastly the Iron Age (where iron and steel objects were made by heating iron ore and adding other material -- like charcoal -- to strengthen it). The Iron Age is usually placed at 1200-1000 BC, yet we have iron nails being used in this extremely old construction
But Wait... There's More!
The most surprising find was discovered with sensitive metal detectors. The team located several strong "hits" that, when dug up, revealed large disc shaped rivets. From simple observation of the metal it was possible to see where the rivet had been hammered after being inserted through a hole [below].

Photo: http://www.viewzone.com/noahx.html
If rivets being used in ancient construction doesn't impress you, this surely will.
An analysis of the metal used to make the rivets revealed that they were a combination of iron (8.38%), aluminum (8.35%) and titanium (1.59%). Remember these trace metals have survived petrification and so do not indicate the exact content in the original material. (see Report from Galbraith Labs)
We know the aluminum was incorporated in the metallic mixture because it does not exist in metallic form in nature. This implies an extremely advanced knowledge of metallurgy and engineering. Characteristics of an iron-aluminum alloy have been investigated in The Russian Chemical Bulletin (2005) and reveal that this alloy forms a thin film of aluminum oxide which protects the material from rust and corrosion. The addition of titanium would provide added strength. This seems to have worked. The rivets have survived from antiquity!
The Surrounding Areas
Several miles from the location of the Ark, huge stones were discovered, some standing upright while others lying on the ground. These stones, weighing many tons, have holes carved in them. Scientists have determined that they were anchors and the holes would have been their attachment to a ship with hemp rope.

Photo: http://www.viewzone.com/noahx.html
Often these stones will have crosses carved in them, from centuries ago when pilgrims made the journey to visit the Ark. Yes, the Ark was well known in the Middle Ages and even before. And its location was recorded in many historical documents.
"And the Ark rested in the seventh month, on the seventeenth day of the month, upon the mountains of Ararat. And the waters decreased continually until the tenth month: in the tenth month, on the first day of the month, were the tops of the mountains seen." - Genesis 8:4-5
The Gilgamesh Epic (650 BC) gives Mt. Nisir as the landing place of the Ark. The local name for the town where the Ark was found is Nasar.
The annals of Ashurnasurpal II of Assyria (833-859 BC) places it south of the Zab river (correct).
Theophilus of Antioch (115-185 AD) said the Ark could be seen in his day in the Arabian mountains. Later Church Fathers also mention the Ark as late as the mid 7th century.
In the 13th century, Willam, a traveler, stated for the first time that Mt. Masis was the Ark location (present-day Mt. Ararat).
Ptolemy's Geographia (1548) mentions the mountains of Armenia as the place of landing. So does the traveler Nicolas de Nicolay (1558).
Pilgrims to the site would gather bits and pieces of the petrified wood which would be used as charms to ward off evil. When they encountered the anchors, they had no doubt about their association with the Ark. They often carved one big cross to represent Noah and smaller crosses representing his family.

Photo: http://www.viewzone.com/noahx.html
The huge anchors would have been suspended from the keel of the ship. This was a common practice among ancient mariners to stabilize a heavy ship and ensure that the bow is always facing the on-coming waves. A "top heavy" ship, such as the Ark, could easily be capsized by a wave approaching from the side. This is yet further proof that Noah's Ark was a reality and that it has indeed been found in Turkey.
Source / By Dan Eden
 Earlier in the week, we detailed JPMorgan's attempt to create their own "web cash" alternative to Bitcoin (and Sberbank's talk of doing the same). However, as M-Cam details, following the failure of the first 154 'claims', JPMorgan issued a further 20 claims - which were summarily rejected (making JPMorgan 0-175 for approved claims). As they note, The United States Patent & Trademark Office (USPTO)’s handling of applications like JPMorgan’s ‘984 application ("Bitcoin Alternative") highlights the need to fix a broken system - patent applications of existing inventions need to be finally rejected and not be resurrected as zombies (no matter how powerful the claimant).
Earlier in the week, we detailed JPMorgan's attempt to create their own "web cash" alternative to Bitcoin (and Sberbank's talk of doing the same). However, as M-Cam details, following the failure of the first 154 'claims', JPMorgan issued a further 20 claims - which were summarily rejected (making JPMorgan 0-175 for approved claims). As they note, The United States Patent & Trademark Office (USPTO)’s handling of applications like JPMorgan’s ‘984 application ("Bitcoin Alternative") highlights the need to fix a broken system - patent applications of existing inventions need to be finally rejected and not be resurrected as zombies (no matter how powerful the claimant).
“BITCOIN is booming.”...?
On August 5, 2013 JPMorgan Chase & Co (JPMorgan) filed an application for an electronic mobile payment system which has eerie similarities to the popular online currency Bitcoin. Unfortunately for JPMorgan, all of the claims, totaling 175 claims, as of October 18, 2013, for published US patent application 20130317984 (the ‘984 application) have been either cancelled or rejected.
Analysis
Below is a view of JPMorgan’s ‘984 application.

After the initial 154 claims were abruptly cancelled, JPMorgan’s attorney submitted 20 additional claims which the examiner, Jagdish Patel, issued non?final rejections for all 20 of the new claims in October 2013. This makes JPMorgan 0?175 in terms of approved claims. The last 20 claims were rejected for non?patentability and indefiniteness under Title 35 United States Code (U.S.C.) Sections 101 and 112.
However, Mr. Patel might well have rejected the claims because of the ‘On Sale Bar’ rule under 35 U.S.C. Section 102(b), meaning that if the invention has been on sale for over a year then the invention is no longer patentable. Under the ‘On Sale Bar’ rule, the application could be invalid because it closely mirrors Bitcoin with features such as making free and anonymous electronic payments and Bitcoin has been in circulation since 2009.
Conclusion
The United States Patent & Trademark Office (USPTO)’s handling of applications like JPMorgan’s ‘984 application highlights the need to fix a broken system.
Patent applications of existing inventions need to be finally rejected and not be resurrected as zombies.
Part of the problem of a system in which one third of patents are seriously or fatally impaired is that companies are allowed to patent items that their competitors have already invented.
Obviously, large financial institutions want in on the online alternative currency action. But they would be well advised to pursue novel and non?obvious approaches that do not duplicate existing commercial options with respect to a virtual medium of exchange.

(Truthstream Media)
Google has announced that it has purchased Boston Dynamics, the engineering firm which has produced all those creepy dystopian future robots for the Defense Advanced Research Projects Agency (DARPA), such as the Big Dog (a dog robot that can throw cinder blocks with an arm coming out of its head), Cheetah (the world’s fastest sprinting robot that can outpace humans) and Atlas (the one that’s eerily reminiscent of something out of a Terminator film…Skynet, anyone?).
The Times of India reports:
The deal is also the clearest indication yet that Google is intent on building a new class of autonomous systems that might do anything from warehouse work to package delivery and even elder care.
So Google is building a new class of autonomous systems that might do anything… To that end, Boston Dynamics is now the eighth robotics firm Google has bought over the past six months.
The search engine giant has been tight-lipped so far about what exactly it plans to do with all of these robots, but it is clear that Boston Dynamics is spearheading a revolution — a robotic revolution.
Gee. Great.
According to the Google exec who lead the Android effort Andy Rubin, the company’s robotics push is a “moonshot” — alluding to a grand scale project that could transform the landscape — but he has declined to comment any further. For Rubin, Boston Dynamics’ climbing, jumping and running array of machines are part of an emerging wave of autonomous machines, commenting that, “computers are starting to sprout legs and move around in the environment.”
Should Google’s latest purchase be a tad more than a little disconcerting to the average person? Multiple reasons why it should immediately come to mind:
1. Google is totally in bed with DARPA and the U.S. government.
Google, a company with a CEO quoted as saying things like “We know where you are. We know where you’ve been. We can more or less know what you’re thinking about,” and “The Internet of things will augment your brain,” has strong ties to the U.S. government, particularly the CIA and NSA. The Corbett Report noted that, “In 2006, ex-CIA officer Robert David Steele told Homeland Security Today that Google “has been taking money and direction for elements of the US Intelligence Community, including the Office of Research and Development at the Central Intelligence Agency, In-Q-Tel, and in all probability, both the National Security Agency (NSA) and the Army’s Intelligence and Security Command.”
DARPA is the Department of Defense’s research arm, complete with creepy projects that run the gamut from mind controlling a squid to change its colors to genetically engineering humans by adding a 47th chromosome. The two are already quite familiar with each other. In fact, former DARPA Director Regina Dugan left her post to take an executive position leading Google subsidiary Motorola’s special projects, and she has since made appearances to show off the new smart tattoos they’ve developed that can authenticate a person’s body like an Internet password.
In addition, Google has announced it will continue all current government contracts at Boston Dynamics.
2. Ray Kurzweil. Just Ray Kurzweil.
Kurzweil, the leading proponent of the singularity and transhumanism and someone who is all about reverse-engineering the human brain to create artificial intelligence, took a position as Director on Engineering with Google in December 2012. Guess what Kurzweil will be focusing on at Google. Just take a wild guess. If you picked artificial intelligence, you win a gold star.
Kurzweil has openly admitted he is all about ushering in a transhumanist future where AI computer entities are given bodies, where the minds of humans are transplanted into mechanical vessels and more. (See the Global Future 2045 project and Kurzweil discussing how we’ll all be immortal by 2045 for more on that.)
A firm like Boston Dynamics would obviously be part of Kurzweil’s future vision dream team (and all come from the common wellspring of MIT.)
3. Terminator: Will Google become the real-life sentient evil computer network Skynet?
Here’s some food for thought on this cleverly illustrated by Dejan SEO (even though we’ve all been thinking it for years now):
…And we haven’t even fully explored the part where the robots turn against the humans in a bloody futuristic war.
While we’re on the topic of supposedly fictional movie plots coming true, it bears repeating that Google has already purchased seven other robotics firms just in the last six months alone.
If Google’s track record and current actions don’t sound like the perfect recipe for an exquisite and terrifying cybernetic revolt disaster, we’re not sure what is. See also the plot of The Matrix Trilogy.
Another film that comes to mind is Avatar, where robotic bodies are used by the military as a force multiplier. DARPA even currently has a $7 million project creatively codenamed “Avatar” with a goal of… wait for it… building robot surrogates for humans.
And those are just the three things that immediately came to our minds when we read the Google Boston Dynamics buyout headline…
(Let’s not even get started on the fact that ubiquitous smarter, faster and cheaper robots will ultimately mean less human jobs; that’s a whole other article entirely. Dystopic future here we come!)

Screenshot of parts of slides from an internal NSA presentation published by the Washington Post (Image credit: Washington Post)
This comes after it was revealed on Monday that the NSA and GCHQ spy on online games. Last month, it was reported that a secret deal allows the NSA to spy on UK citizens who are not suspected of any wrongdoing.
The latest revelations came in the form of an internal NSA presentation, which shows that “when companies follow consumers on the Internet to better serve them advertising, the technique opens the door for similar tracking by the government,” according to The Washington Post.
The Post notes that this information could very well shift the debate over consumer privacy and Internet cookies, which continues to rage as technology becomes increasingly advanced.
The NSA and GCHQ are both reportedly using cookies that enable websites to identify a person’s browser and allow the user to be tracked across the web.
The Post reports that the Google tracking mechanism known as the “PREF” cookie “allows NSA to single out an individual’s communications among the sea of Internet data in order to send out software that can hack that person’s computer.”
The documents show that the NSA is also using commercially harvested information to help the agency geolocate mobile devices around the globe. This location information is much more precise than that collected from cellphone networks, according to the Post.
The NSA declined to comment on the tactics outlined in the documents and Google declined to comment to the Post for the article.
However, the NSA maintained that it is well within its mandate when conducting this type of surveillance.
“As we’ve said before, NSA, within its lawful mission to collect foreign intelligence to protect the United States, uses intelligence tools to understand the intent of foreign adversaries and prevent them from bringing harm to innocent Americans,” an NSA spokesman said to the Post.
Of the 25 companies with the largest corporate profits in the world; banking, energy and technology firms are absolutely raking it in. Despite stagnating incomes, these companies made $567,856,000,000 in 2012 alone... here's the subsidies, tax breaks, and offshoring that helped them do it...
Source: AccountingSchoolGuide.com

When do scientific advances cross the line between exciting progress over to a frightening chapter in a futuristic fantasy novel? How about when those advances intrude uncomfortably into the human brain, harvesting thoughts and recording them?
A group of researchers at Stanford University have taken this leap into mad science with experimental “intracranial recording”. Or, put simply, they’ve taken the first step towards mind reading using electronic monitoring of brain activity.
Using a novel method, the researchers collected the first solid evidence that the pattern of brain activity seen in someone performing a mathematical exercise under experimentally controlled conditions is very similar to that observed when the person engages in quantitative thought in the course of daily life.
“We’re now able to eavesdrop on the brain in real life,” said Josef Parvizi, MD, PhD, associate professor of neurology and neurological sciences and director of Stanford’s Human Intracranial Cognitive Electrophysiology Program…
His team’s method, called intracranial recording, provided exquisite anatomical and temporal precision and allowed the scientists to monitor brain activity when people were immersed in real-life situations…
The procedure involves temporarily removing a portion of a patient’s skull and positioning packets of electrodes against the exposed brain surface. For up to a week, patients remain hooked up to the monitoring apparatus while the electrodes pick up electrical activity within the brain…
During this whole time, patients remain tethered to the monitoring apparatus and mostly confined to their beds. But otherwise, except for the typical intrusions of a hospital setting, they are comfortable, free of pain and free to eat, drink, think, talk to friends and family in person or on the phone, or watch videos.
The electrodes implanted in patients’ heads are like wiretaps, each eavesdropping on a population of several hundred thousand nerve cells and reporting back to a computer.
In the study, participants’ actions were also monitored by video cameras throughout their stay. This allowed the researchers later to correlate patients’ voluntary activities in a real-life setting with nerve-cell behavior in the monitored brain region…
Afterward, Parvizi and his colleagues analyzed each volunteer’s daily electrode record, identified many spikes in intraparietal-sulcus activity that occurred outside experimental settings, and turned to the recorded video footage to see exactly what the volunteer had been doing when such spikes occurred…
“These nerve cells are not firing chaotically,” he said. “They’re very specialized, active only when the subject starts thinking about numbers. When the subject is reminiscing, laughing or talking, they’re not activated.” Thus, it was possible to know, simply by consulting the electronic record of participants’ brain activity, whether they were engaged in quantitative thought during nonexperimental conditions. (source)
Researchers are able to suggest all sorts of do-gooder applications for this technology: allowing stroke victims who can’t talk to communicate, for example.
But it isn’t a stretch at all to believe that this will one day be used in a more sinister fashion. It could be applied as a control mechanism, the basis of Big Brother technology like implantable chips for the human brain, or an interrogation tool. Would you really want someone to be able to take the very thoughts from your mind and interpret them?
Henry Greely, JD, the Deane F. and Kate Edelman Johnson Professor of Law and steering committee chair of the Stanford Center for Biomedical Ethics, who is familiar with the study, waved off concerns about mind control. “Practically speaking, it’s not the simplest thing in the world to go around implanting electrodes in people’s brains. It will not be done tomorrow, or easily, or surreptitiously.”

Three years ago, security consultant Dragos Ruiu was in his lab when he noticed something highly unusual: his MacBook Air, on which he had just installed a fresh copy of OS X, spontaneously updated the firmware that helps it boot. Stranger still, when Ruiu then tried to boot the machine off a CD ROM, it refused. He also found that the machine could delete data and undo configuration changes with no prompting. He didn't know it then, but that odd firmware update would become a high-stakes malware mystery that would consume most of his waking hours.
In the following months, Ruiu observed more odd phenomena that seemed straight out of a science-fiction thriller. A computer running the Open BSD operating system also began to modify its settings and delete its data without explanation or prompting. His network transmitted data specific to the Internet's next-generation IPv6 networking protocol, even from computers that were supposed to have IPv6 completely disabled. Strangest of all was the ability of infected machines to transmit small amounts of network data with other infected machines even when their power cords and Ethernet cables were unplugged and their Wi-Fi and Bluetooth cards were removed. Further investigation soon showed that the list of affected operating systems also included multiple variants of Windows and Linux.
"We were like, 'Okay, we're totally owned,'" Ruiu told Ars. "'We have to erase all our systems and start from scratch,' which we did. It was a very painful exercise. I've been suspicious of stuff around here ever since."
In the intervening three years, Ruiu said, the infections have persisted, almost like a strain of bacteria that's able to survive extreme antibiotic therapies. Within hours or weeks of wiping an infected computer clean, the odd behavior would return. The most visible sign of contamination is a machine's inability to boot off a CD, but other, more subtle behaviors can be observed when using tools such as Process Monitor, which is designed for troubleshooting and forensic investigations.
Another intriguing characteristic: in addition to jumping "airgaps" designed to isolate infected or sensitive machines from all other networked computers, the malware seems to have self-healing capabilities.
"We had an air-gapped computer that just had its [firmware] BIOS reflashed, a fresh disk drive installed, and zero data on it, installed from a Windows system CD," Ruiu said. "At one point, we were editing some of the components and our registry editor got disabled. It was like: wait a minute, how can that happen? How can the machine react and attack the software that we're using to attack it? This is an air-gapped machine and all of a sudden the search function in the registry editor stopped working when we were using it to search for their keys."
Over the past two weeks, Ruiu has taken to Twitter, Facebook, and Google Plus to document his investigative odyssey and share a theory that has captured the attention of some of the world's foremost security experts. The malware, Ruiu believes, is transmitted though USB drives to infect the lowest levels of computer hardware. With the ability to target a computer's Basic Input/Output System (BIOS), Unified Extensible Firmware Interface (UEFI), and possibly other firmware standards, the malware can attack a wide variety of platforms, escape common forms of detection, and survive most attempts to eradicate it.
But the story gets stranger still. In posts here, here, and here, Ruiu posited another theory that sounds like something from the screenplay of a post-apocalyptic movie: "badBIOS," as Ruiu dubbed the malware, has the ability to use high-frequency transmissions passed between computer speakers and microphones to bridge airgaps.
At times as I've reported this story, its outline has struck me as the stuff of urban legend, the advanced persistent threat equivalent of a Bigfoot sighting. Indeed, Ruiu has conceded that while several fellow security experts have assisted his investigation, none has peer reviewed his process or the tentative findings that he's beginning to draw. (A compilation of Ruiu's observations is here.)
Also unexplained is why Ruiu would be on the receiving end of such an advanced and exotic attack. As a security professional, the organizer of the internationally renowned CanSecWest and PacSec conferences, and the founder of the Pwn2Own hacking competition, he is no doubt an attractive target to state-sponsored spies and financially motivated hackers. But he's no more attractive a target than hundreds or thousands of his peers, who have so far not reported the kind of odd phenomena that has afflicted Ruiu's computers and networks.
In contrast to the skepticism that's common in the security and hacking cultures, Ruiu's peers have mostly responded with deep-seated concern and even fascination to his dispatches about badBIOS.
"Everybody in security needs to follow @dragosr and watch his analysis of #badBIOS," Alex Stamos, one of the more trusted and sober security researchers, wrote in a tweet last week. Jeff Moss—the founder of the Defcon and Blackhat security conferences who in 2009 began advising Department of Homeland Security Secretary Janet Napolitano on matters of computer security—retweeted the statement and added: "No joke it's really serious." Plenty of others agree.
"Dragos is definitely one of the good reliable guys, and I have never ever even remotely thought him dishonest," security researcher Arrigo Triulzi told Ars. "Nothing of what he describes is science fiction taken individually, but we have not seen it in the wild ever."
Triulzi said he's seen plenty of firmware-targeting malware in the laboratory. A client of his once infected the UEFI-based BIOS of his Mac laptop as part of an experiment. Five years ago, Triulzi himself developed proof-of-concept malware that stealthily infected the network interface controllers that sit on a computer motherboard and provide the Ethernet jack that connects the machine to a network. His research built off of work by John Heasman that demonstrated how to plant hard-to-detect malware known as a rootkit in a computer's peripheral component interconnect, the Intel-developed connection that attaches hardware devices to a CPU.
It's also possible to use high-frequency sounds broadcast over speakers to send network packets. Early networking standards used the technique, said security expert Rob Graham. Ultrasonic-based networking is also the subject of a great deal of research, including this project by scientists at MIT.
Of course, it's one thing for researchers in the lab to demonstrate viable firmware-infecting rootkits and ultra high-frequency networking techniques. But as Triulzi suggested, it's another thing entirely to seamlessly fuse the two together and use the weapon in the real world against a seasoned security consultant. What's more, use of a USB stick to infect an array of computer platforms at the BIOS level rivals the payload delivery system found in the state-sponsored Stuxnet worm unleashed to disrupt Iran's nuclear program. And the reported ability of badBIOS to bridge airgaps also has parallels to Flame, another state-sponsored piece of malware that used Bluetooth radio signals to communicate with devices not connected to the Internet.
"Really, everything Dragos reports is something that's easily within the capabilities of a lot of people," said Graham, who is CEO of penetration testing firm Errata Security. "I could, if I spent a year, write a BIOS that does everything Dragos said badBIOS is doing. To communicate over ultrahigh frequency sound waves between computers is really, really easy."
Coincidentally, Italian newspapers this week reported that Russian spies attempted to monitor attendees of last month's G20 economic summit by giving them memory sticks and recharging cables programmed to intercept their communications.
For most of the three years that Ruiu has been wrestling with badBIOS, its infection mechanism remained a mystery. A month or two ago, after buying a new computer, he noticed that it was almost immediately infected as soon as he plugged one of his USB drives into it. He soon theorized that infected computers have the ability to contaminate USB devices and vice versa.
"The suspicion right now is there's some kind of buffer overflow in the way the BIOS is reading the drive itself, and they're reprogramming the flash controller to overflow the BIOS and then adding a section to the BIOS table," he explained.
He still doesn't know if a USB stick was the initial infection trigger for his MacBook Air three years ago, or if the USB devices were infected only after they came into contact with his compromised machines, which he said now number between one and two dozen. He said he has been able to identify a variety of USB sticks that infect any computer they are plugged into. At next month's PacSec conference, Ruiu said he plans to get access to expensive USB analysis hardware that he hopes will provide new clues behind the infection mechanism.
He said he suspects badBIOS is only the initial module of a multi-staged payload that has the ability to infect the Windows, Mac OS X, BSD, and Linux operating systems.

To put it another way, he said, badBIOS "is the tip of the warhead, as it were."
Ruiu said he arrived at the theory about badBIOS's high-frequency networking capability after observing encrypted data packets being sent to and from an infected laptop that had no obvious network connection with—but was in close proximity to—another badBIOS-infected computer. The packets were transmitted even when the laptop had its Wi-Fi and Bluetooth cards removed. Ruiu also disconnected the machine's power cord so it ran only on battery to rule out the possibility that it was receiving signals over the electrical connection. Even then, forensic tools showed the packets continued to flow over the airgapped machine. Then, when Ruiu removed the internal speaker and microphone connected to the airgapped machine, the packets suddenly stopped.
With the speakers and mic intact, Ruiu said, the isolated computer seemed to be using the high-frequency connection to maintain the integrity of the badBIOS infection as he worked to dismantle software components the malware relied on.
"The airgapped machine is acting like it's connected to the Internet," he said. "Most of the problems we were having is we were slightly disabling bits of the components of the system. It would not let us disable some things. Things kept getting fixed automatically as soon as we tried to break them. It was weird."
It's too early to say with confidence that what Ruiu has been observing is a USB-transmitted rootkit that can burrow into a computer's lowest levels and use it as a jumping off point to infect a variety of operating systems with malware that can't be detected. It's even harder to know for sure that infected systems are using high-frequency sounds to communicate with isolated machines. But after almost two weeks of online discussion, no one has been able to rule out these troubling scenarios, either.
"It looks like the state of the art in intrusion stuff is a lot more advanced than we assumed it was," Ruiu concluded in an interview. "The take-away from this is a lot of our forensic procedures are weak when faced with challenges like this. A lot of companies have to take a lot more care when they use forensic data if they're faced with sophisticated attackers."
In a recent report by The Washington Post, it was revealed that the FBI has been able to secretly activate a target’s laptop camera “without triggering the light that lets users know it is recording” for several years.
While this may be surprising to some, it really shouldn’t be. Previous reports revealed that the FBI employs hackers to create software to remotely activate the microphones on laptops and cell phones as well as cameras. The U.S. government has also become the world’s largest buyer of malware. The NSA also recommended physically removing the webcam from Apple laptops for security reasons.
In August, the Wall Street Journal reported that the FBI has developed hacking tools like this for over a decade, though they rarely are discussed publicly.
The Washington Post cites Marcus Thomas, former assistant director of the FBI’s Operational Technology Division in Quantico, who said that the remote activation of cameras is used mostly in serious cases.
Thomas, who now sits on the advisory board of Subsentio, a company that helps telecommunications firms comply with federal wiretap laws, told the Post that the bureau uses the technique “mainly in terrorism cases or the most serious criminal investigations.”
As technology advances, the FBI’s surveillance techniques do as well.
“Because of encryption and because targets are increasingly using mobile devices, law enforcement is realizing that more and more they’re going to have to be on the device — or in the cloud,” Thomas said.
Indeed, in January of this year a report indicated that all data stored on cloud services could be accessed by the U.S. government without a warrant.
In the past, a federal magistrate rejected the FBI’s attempt to get authorization to activate the laptop camera of a suspect. The magistrate ruled that it was “extremely intrusive” and could be a violation of the Fourth Amendment.
Federal magistrate Judge Stephen W. Smith also said the Texas-based court did not have the jurisdiction to approve the search of a computer in an unknown location.
Yet, another federal magistrate approved sending surveillance software to a target, though it did not involve remotely activating a computer camera.
The surveillance software gave the FBI a detailed account of the computer of the target – a federal fugitive – including his hard drive space, the chips used on his computer and a list of installed programs.
In the case the Post was reporting on, an individual calling himself “Mo,” probably located in Tehran, made a series of bomb threats.
The FBI obtained a warrant to send surveillance software to Mo’s computer when he sign in to his Yahoo email account but the program “never actually executed as designed,” according to a handwritten note by a federal agent given to a court.
Thanks to the internet, the availability of parts and materials, and good old-fashioned ingenuity, there is a wide range of in-home, and in-apartment, gardening systems that are easy to construct and maintain, and that can provide nutritious, organic, and low-cost food for you and your family. Once you realize jut how rewarding home gardening can be, it is tremendously fun to experiment with different systems and ideas for best producing your favorite healthy, fresh fruits and veggies.
Since everyone’s gardening space, interests and budgets differ, here are 10 simple ideas and how to’s for getting a small, affordable, and easy to construct gardening system up and running in your home.
Aquaponics is growing in popularity as a versatile method of growing nutritious vegetables while raising fish, combining hydroponic gardening with aquaculture. Systems can be built to fit in almost any location, indoors or outdoors, and can be designed for almost any crop or edible fish.
Read: Aquaponic Gardening: A Step-By-Step Guide to Raising Vegetables and Fish Together
Here is a simple affordable home aquaponics system that can be adapted. Be sure to read the comments below the video for additional insight and afterthoughts on this simple system…
This is a great example of an apartment size indoor aquaponics system…
Vertical gardening is a terrific method of growing more plants in a smaller area by constructing standing or hanging planters that can house many plants in a small space.
The easy and affordable example below can be adapted for many different fruits and veggies, or scaled for larger purposes…
The following video is an example of a simple and cheap, stand-up pallet vertical garden…
Greenhouses are imperative for starting many types of edible plants and can also offer protection against some garden pests while increasing the length of your growing season.
Easy to build hoop house green house how-to…
How to build a backyard fence-rested greenhouse…
Cold frames are an excellent and affordable way of growing nutritious ground crops in colder climates and during the winter…
Simple winter cold frame garden…
Composting is an essential part of every garden, is the best way to dispose of everyday organic kitchen refuse, and provides free plant-food for your garden.
Read: Let it Rot!: The Gardener’s Guide to Composting (Third Edition) (Storey’s Down-To-Earth Guides)
3-bin compost system using free pallets…
Cheap do-it-yourself worm composter…
Living in an apartment can mean you have to be more creative and imaginative with the space you have. Here are some resources and ideas for finding and setting up your apartment garden.
Read: Apartment Gardening: Plants, Projects, and Recipes for Growing Food in Your Urban Home
Here are some useful tips on finding space for your apartment garden…
We hope that you find the inspiration to find out for yourself just how easy, fun, and liberating home gardening can be as further stress on our collective food systems continues to drive up prices and drive down nutrition.
Gardening is both addictive and contagious, so be prepared to have fun, grow some tasty food, and meet some new friends once your neighbors hear about your success.